Drupal Security Updates: 12-18-2019
Drupal is one of the most secure Web Content Management systems available today and the credit for this goes to the simple fact that there is a dedicated security team that constantly checks the codebase for any vulnerabilities and provides fixes for any vulnerabilities identified.
As per the Drupal Security team, security release "windows" are every Wednesday for Drupal contributed projects, and one Wednesday a month (usually the third Wednesday) for Drupal core.
As a site owner, it is really important to monitor the security releases regularly and apply the relevant security patches the same day itself or schedule for it based on the criticality of the update.
Latest Secure Drupal Versions
- Drupal Core 7.x: 7.69 released on December 18th 2019
- Drupal Core 8.8.x: 8.8.1 released on December 18th 2019
- Drupal Core 8.7.x: 8.7.11 released on December 18th 2019
Any 8.x versions older than 8.7 should be updated to latest 8.8.x or 8.7.x
If you are not using the latest versions, it is recommended to update the core to the latest release as soon as possible to avoid possible security breaches.
Security Alert
If you are not using the latest versions, it is recommended to update the core to the latest release as soon as possible to avoid possible security breaches.
There are few security alerts published by the Drupal security team on 18th December 2019, which include some critical and moderately critical security updates. It is really important to act on this immediately
Here are the reported vulnerabilities.
SA-CORE-2019-009 - Denial of Service
Affected versions : 8.8.x, 8.7.x
Security risk: Moderately critical
A visit to install.php can cause cached data to become corrupted. This could cause a site to be impaired until caches are rebuilt.
SA-CORE-2019-010 - Multiple vulnerabilities
Affected versions : 8.8.x, 8.7.x
Security risk: Moderately critical
Drupal 8 core's file_save_upload() function does not strip the leading and trailing dot ('.')
from filenames, like Drupal 7 did.
Users with the ability to upload files with any extension in conjunction with contributed modules may be able to use this to upload system files such as .htaccess in order to bypass protections afforded by Drupal's default .htaccess file.
After this fix, file_save_upload() now trims leading and trailing dots from filenames.
SA-CORE-2019-011 - Access bypass
Affected versions : 8.8.x, 8.7.x
Security risk: Moderately critical
The Media Library module has a security vulnerability whereby it doesn't sufficiently restrict access to media items in certain configurations.
SA-CORE-2019-012 - Multiple vulnerabilities
Affected versions : 8.8.x, 8.7.x, 7.x
Security risk: Critical
The Drupal project uses the third-party library Archive_Tar, which has released a security-related feature that impacts some Drupal configurations.
Multiple vulnerabilities are possible if Drupal is configured to allow .tar, .tar.gz, .bz2 or .tlz file uploads and processes them. The latest versions of Drupal update Archive_Tar to 1.4.9 to mitigate the file processing vulnerabilities.
Solution: Install the latest version of Drupal
If you are using Drupal 8.7.x, upgrade to Drupal 8.7.11.
If you are using Drupal 8.8.x, upgrade to Drupal 8.8.1.
If you are using Drupal 7.x, upgrade to Drupal 7.69.
Checklist for Site Owners who Need to Update Immediately
Is your install.php accessible for external users?
Are you allowing users to upload files?
Are you using media library?
If the answer to any of these questions is “Yes” you have to immediately update to the latest version. Even if the answer is ‘no’, the security best practices say it is always good to update the latest security releases to avoid risks.
End of Life Plans for Drupal 7.x and 8.x
Drupal 7.x will reach end of life on November 2021.
What this means for your Drupal 7 sites is, as of November 2021:
- There will be no more core commits to Drupal 7.
- The Drupal Security Team will no longer provide support or Security Advisories for Drupal 7 core or contributed modules, themes, or other projects. Reports about Drupal 7 vulnerabilities might become public creating 0 day exploits.
- All Drupal 7 releases on all project pages will be flagged as not supported. Maintainers can change that flag if they desire to.
- On Drupal 7 sites with the update status module, Drupal Core will show up as unsupported.
- After November 2021, using Drupal 7 may be flagged as insecure in 3rd party scans as it no longer gets support.
- Best practice is to not use unsupported software, it would not be advisable to continue to build new Drupal 7 sites.
- Now is the time to start planning your migration to Drupal 8.
Drupal 8 will reach end of life on November 2021.
Drupal 8 will reach EOL the same day of Drupal 7 EOL. If you are already using Drupal 8, you don’t have to worry about anything.
- Drupal has adopted to a continuous innovation model since Drupal 8.
- New features are added to Drupal core every 6 months.
- In this process, some systems will be deprecated and will be kept as such.
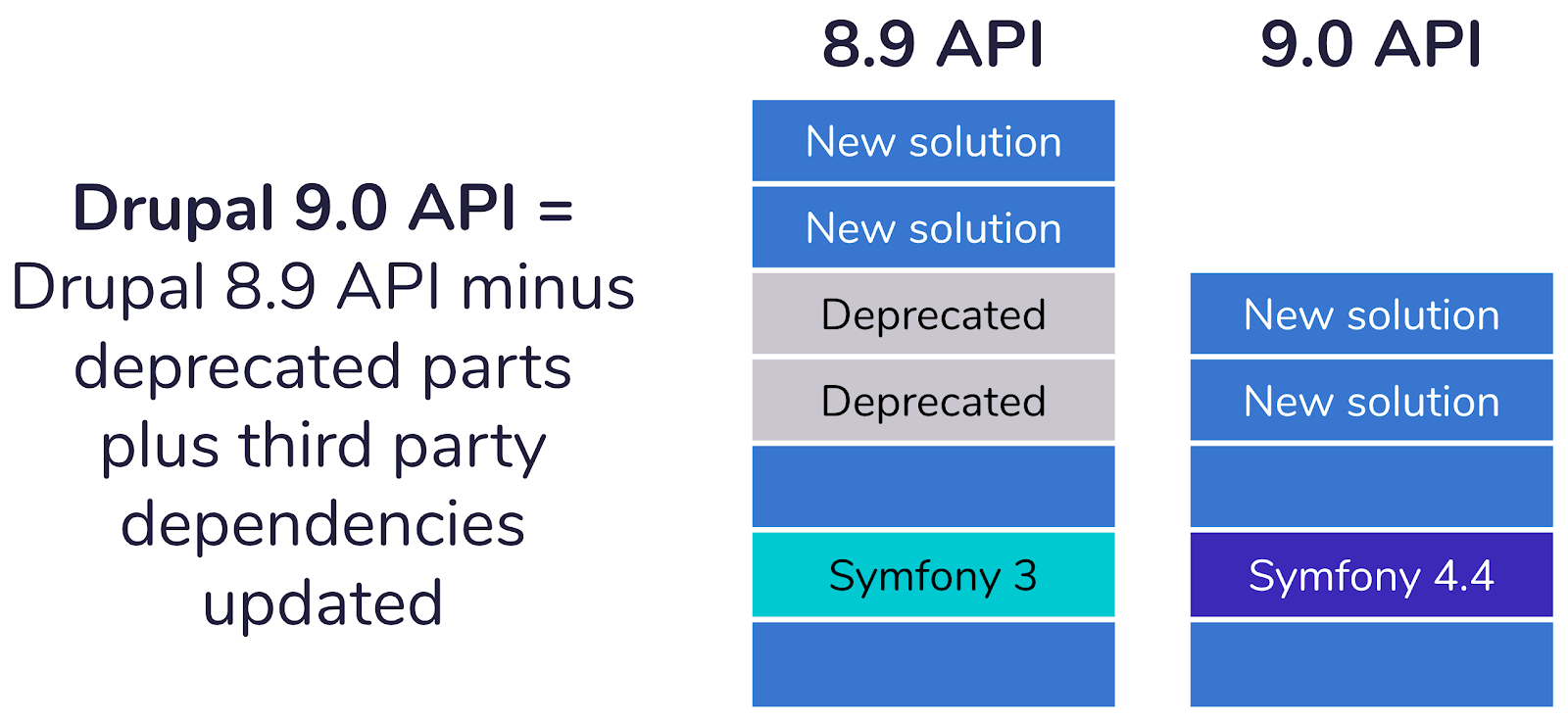
- The more innovations occurs, the more deprecated code will be there, which eventually will be removed and the code will be released as Drupal 9.
- Drupal 9.0 should be almost identical to the last Drupal 8 release which will be Drupal 8.9, minus the deprecated code.
- It means that when modules take advantage of the latest Drupal 8 APIs and avoid using deprecated code, they should work on Drupal 9.
- Updating from Drupal 8's latest version to Drupal 9.0.0 should be as easy as updating between minor versions of Drupal 8.
What Next?
Those who still use Drupal 6.x or 7.x should immediately think of migrating to Drupal 8.9 which will be released in June 2020. Once you migrate to Drupal 8.9, upgrading to Drupal 9.0 when it will be released is as easy as executing a minor update as there will not be any changes in Drupal 9 from Drupal 8.9 except changes in some underlying libraries.
Annexure
Drupal 8 is now power-packed with a handful of features. This include